On my twitter feed, I saw a tweet from Microsoft about Microsoft Flow, Microsoft's tool which says I should
I did know about Microsoft Flow, but never had a need for it. But for some reason my mind connected Microsoft Flow with Troy Hunt's PwnedPasswords service. He's written loads about how it works, and how the API can be used to anonymously check for passwords which he's found in the website breaches he's tracked. I thought...
It'd be great if I could be alerted if the few really secure passwords I have (e.g. my password manager password and email account) are ever found in the PwnedPasswords database
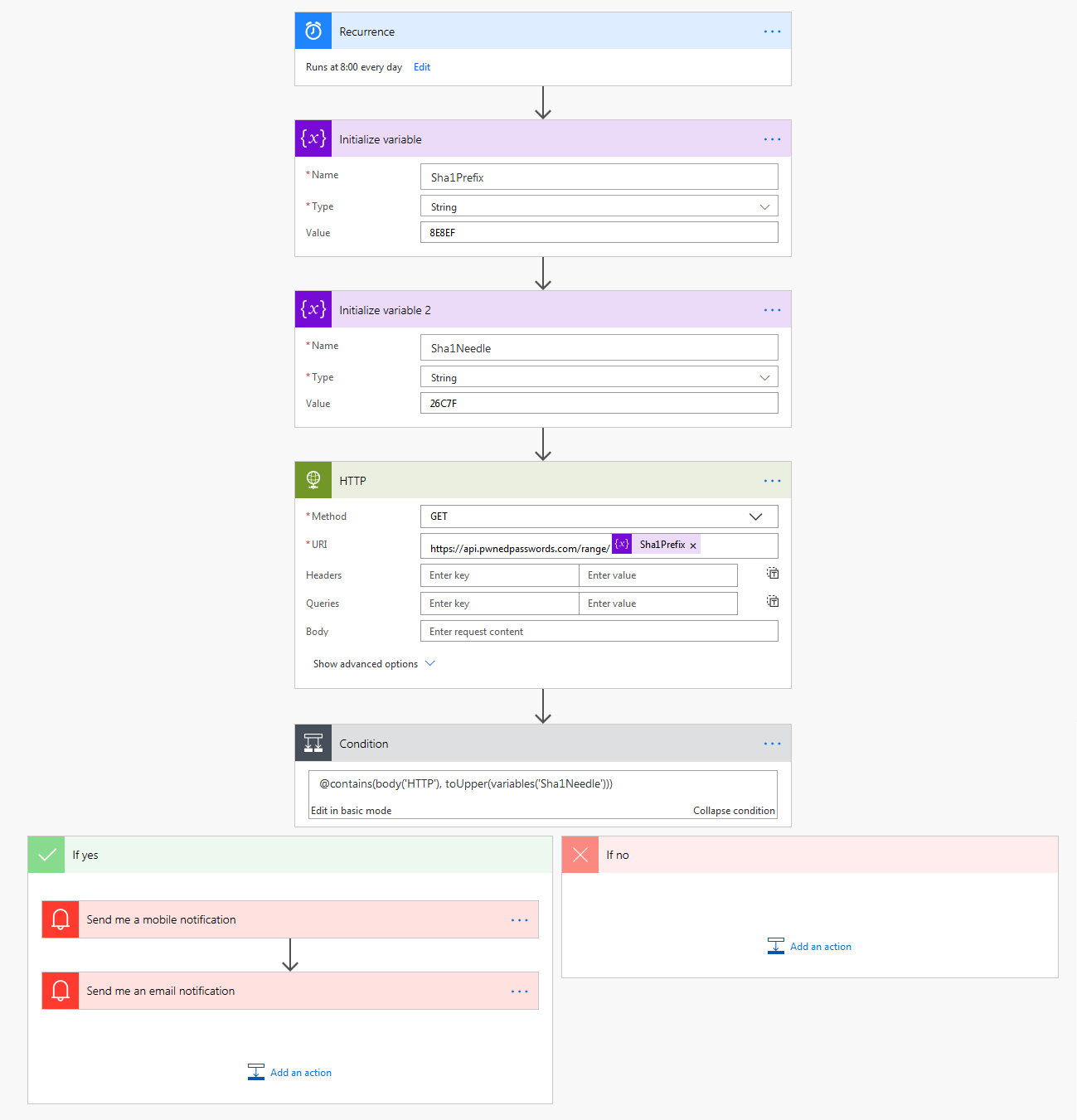
And so, I fired up the site and gave it a go. Here's what I came up with
- Use a recurrence trigger (I have mine for 8am daily)
- Initialize 2 variables:-
a) Sha1Prefix - a string which is the 5 character SHA-1 prefix of my password
b) Sha1Needle - a string which is another X chars of the SHA-1 of my password. I could use all the prefix, but I chose to just use 5 characters of it. As long as it's long enough to not cause any matches it won't cause a false-positive (and so far it hasn't) - Next, I use the HTTP action to query PwnedPasswords API. The API for PwnedPasswords is fairly straight forward and is well documented. A simple HTTP/GET is all that's needed to get the data
- PwnedPassword's API returns all matching SHA-1 suffixes. So I need a condition to check if my Sha1Needle is in the HTTP response body. If it is I send a mobile notification and email to myself, if it doesn't appear then I do nothing.
If you're interested, a screenshot of the flow is shown below if you're curious