OCSP is a protocol which allows clients to verify X509 certificate validity, essentially checking if the certificate has been revoked since issuance
There are privacy concerns which I won't get into too much here, but I was curious what was sent 'on the wire'. As OCSP is checking for certificate validity, it goes to an unencrypted (HTTP) endpoint. If it went to an HTTPS endpoint, a problem exists where it can't check the validity status of the OCSP end-point certificate as it's on an encrypted HTTPS endpoint....etc
So as traffic is going in plain-text, what's actually sent
RFC 2560 describes the protocol and section 4.1.1 has the request laid out
The TLDR; is only the serial number of the certificate is sent, along with the hash of the CA issuers name & key. As such, any evesdropper on the network won't immediately know what certificate (and therefore what site) you're in the process of browsing to (but the CA does - hence the privacy concerns)
But to be sure, I fired up wireshark and checked for myself, using openssl to perform the OCSP check manually
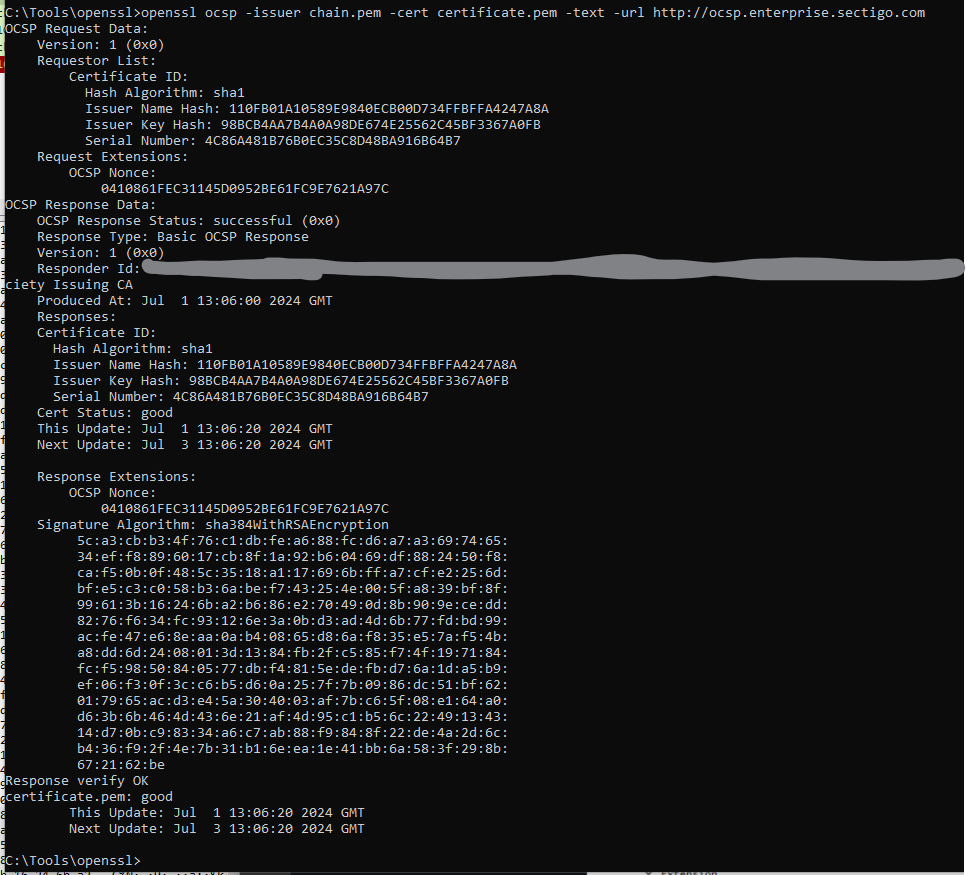
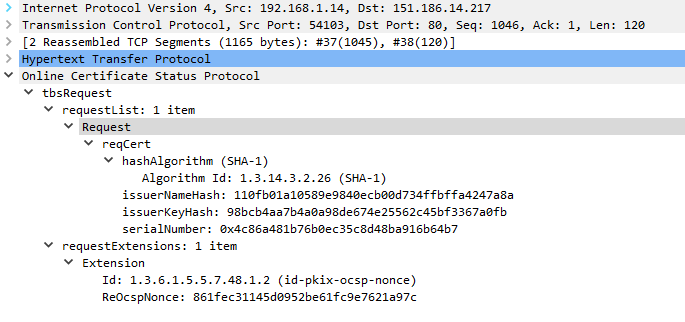
Wireshark's view of the request was as follows:
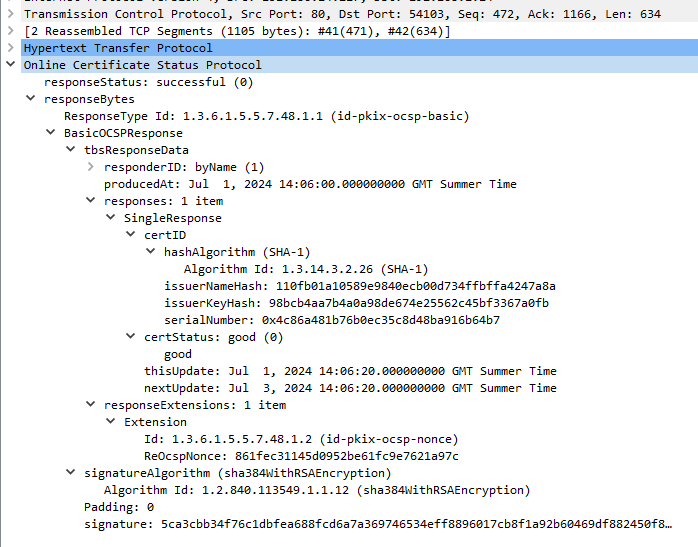
And the response:
So for my current use case (deploying a corporate PKI with an OCSP) this is likely fine. The solution to eliminating the privacy concern is to do OCSP stapling, but that's out of scope for this brief post